Interoperability
What is Interoperability?
Interoperability, as per ECHO definition, is the ability of organizations to interact towards mutually beneficial goals, involving the (secured & safe) sharing of information and knowledge between organizations, through the business processes they support, by means of exchanging data with other systems using common standards
The Vision
The principal objective of the project is:
To enable dignified humanitarian assistance through safe data sharing between organizations and affected individuals The hypothesis of the project is that through research on privacy-protecting technologies and methodologies for sharing data, we can lay the groundwork for humanitarian systems interoperability.
The project has five main activities:
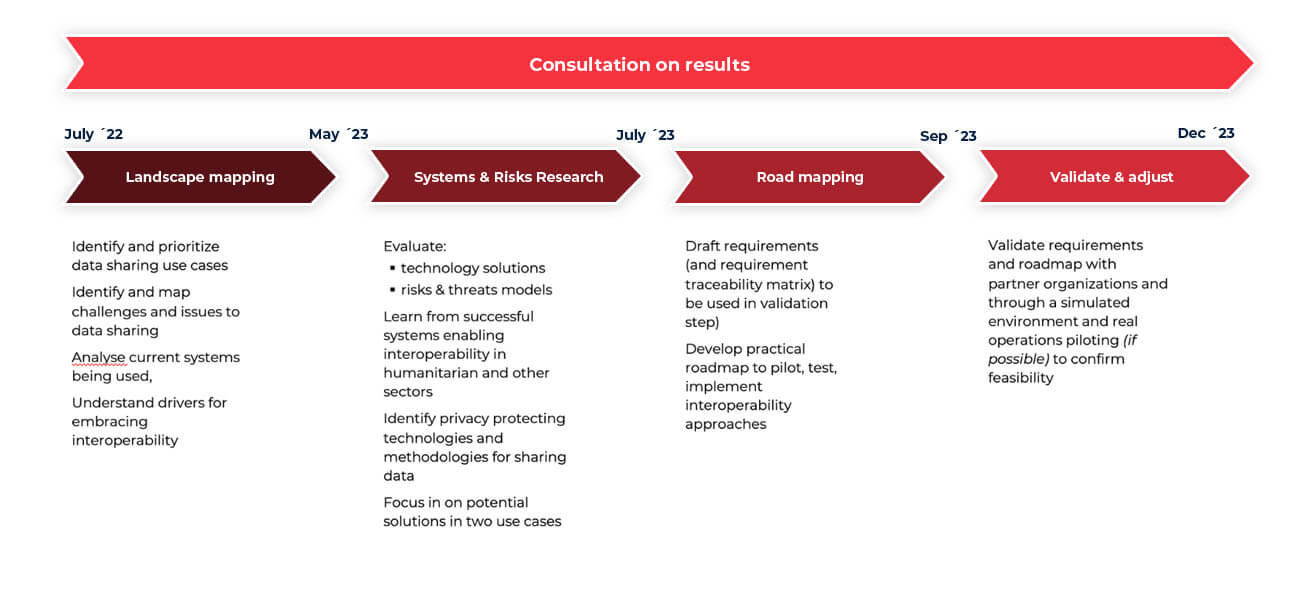
Landscape mapping
Identify (CVA) uses cases and their priority, systems currently used, and map challenges faced to share relevant data.
Systems research
To identify and evaluate technical options to address blockers to data sharing.
Risks and threat models research
To look at Risks in current practices and technical options considered and how to address them.
Draft a set of requirements and an implementation roadmap
Based on findings from the research to guide and expand future collaboration
Validation
Validation with partners organizations, document lessons learned, key insights
Based on the learning from the landscape mapping [Include links to reports] and criteria such as the value delivered to affected people, the level of risk associated with current practice, the complementarity with the CCD work, DIGID has selected the Deduplication and Referral use case for the next step of the project. Referrals include both Organizational referral – Sharing data on which organizations can provide what kind of support to whom, and Individual referral – Sharing data on a person with a partner, donor or government for follow-up services.

Activity 1 –
Landscape mapping
Gather and consolidate information from various sources through desk review and consultations. Will inform the subsequent research and ensure we focus our efforts on the right uses case and most pressing challenges to data sharing.
Activity 1 will seek to increase our understanding of the existing environment:
- Identify and prioritize data-sharing use cases,
- Identify and map challenges and issues to data sharing,
- Analysis of current systems being used,
Understand drivers for organizations to embrace interoperability and how those with limited capacity and digital capability can participate in interoperability.
The focus of this consultation will be on UN agencies, CDD network and RCRC network. Well established but also small organization with limited resources and digital capabilities will be included.

Activity 2 –
Systems research and evaluation
Research privacy protecting technologies and methodologies for sharing data. Identify solutions that best address identified risks in priority uses case while promoting beneficiary control over their data whenever possible.
Activity 2 will seek to clarify the available technology options:
- Identify and learn from successful implementation of systems enabling interoperability in humanitarian and other sectors,
- Identify privacy protecting technologies and methodologies for sharing data (peer to peer/ distributed protocol, data sharing standard, minimum data set…)
- Collaborate with institutions working on standard and digital rights,
- Draft potential solutions requirements.
This research stream will include consultation with other organizations but also relevant academia or private sector companies as needed.

Activity 3 –
Risks and threats model research & evaluation
Research risk and threats model associated with technology being used, organizations, legal…
Activity 3 will seek to clarify the risks and threats model to address and mitigate
- Identify and learn from successful or challenged implementation of systems enabling interoperability in humanitarian and other sectors,
- Identify or build Risks and threats model for technologies relevant to priority use cases,
- Collaborate with institutions working on standard and digital rights,
- Draft data protection and security requirements to mitigate the identified risks and threats.
This research stream will include consultation with other organizations but also relevant academia or private sector companies as needed.

Activity 4 – Draft requirements and implementation roadmap
Draft requirements baseline and an implementation roadmap based on the research. Will be very useful to check feasibility and run validation with the partner organization.
Activity 4 will seek to prepare the content for the validation step
- Draft requirements (and requirement traceability matrix to be used in validation step),
- Draft implementation roadmap

Activity 5 –
Validate, learn, adjust
The most important of all steps will be to validate the proposed requirements and implementation roadmap with selected partners organizations representing the diversity of the humanitarian ecosystem, gather valuable insights and adjust.
Activity 5 will seek to validate the requirements and roadmap through the usage of a simulated environment and real operations piloting (if possible).
- Establish an environment for safe and collaborative testing,
- Conduct table-top testing exercises based on prioritized uses cases, checking the draft requirements within local context,
- Consolidate feedback and insights from partner organizations and representatives from affected communities,
- alidate draft implementation road map to document required follow-up activities, pre-requisites for an organizations to implement, dependencies on other piece of work…
The validation will be run in collaboration with partner organizations.
Project timeline
Deliverables
addressing risks
and barriers to data sharing in
CVA uses cases
CCD project outlining
the way forward
Implementing partners
Acknowledge donors